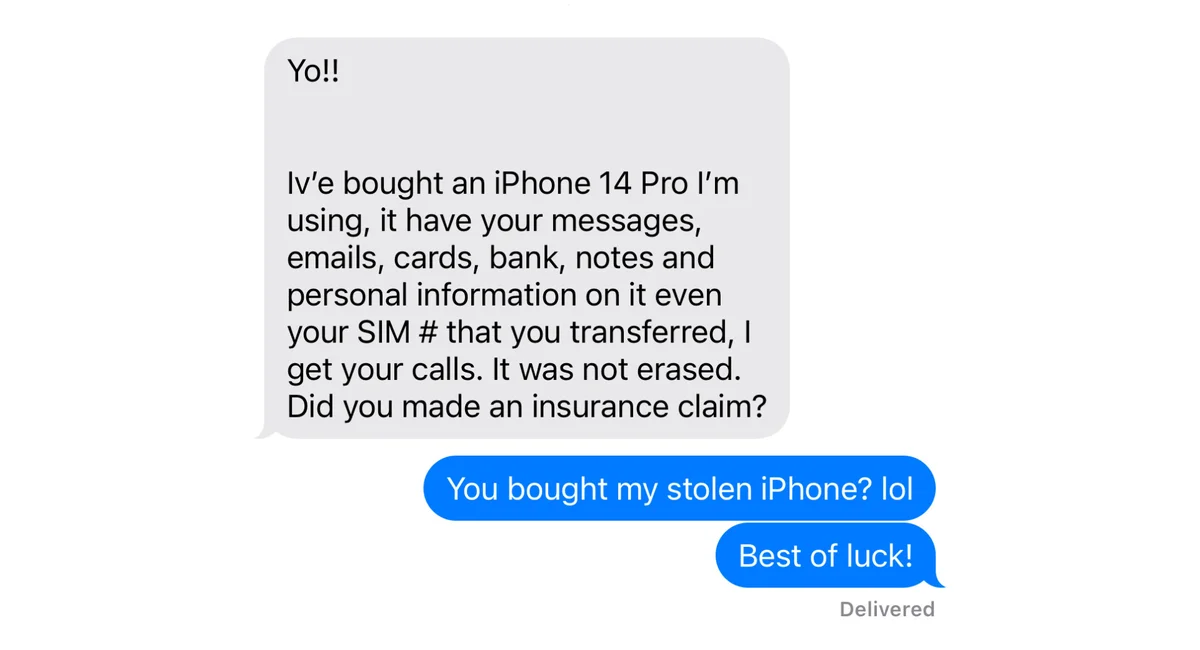
This is a very entertaining and educational article, giving insights into the methods used by thiefs to try and get access to your phone data.
I don’t like Apple but it’s great that their security is so good when it comes to this.
As someone who’s experienced the same thing, some of the messages I received were shockingly well written.
The fake “find my” site they tried to use to convince me to log into my iCloud account was wildly convincing, if not for the index.php at the end of the URL - something Apple would never configure for service endpoints.
They continued to try - but never threatening. However I never engaged and eventually they just stopped trying.
yeah and the said part is most people without the tech background would never notice the index.php in the URL, or care.
Whoa that was a wild ride, worth the read. It’s a sad market that exists, great to see Apple’s privacy and security at work (as an Android user even).
Honestly I’m scared of when these people figure out they can use llms to make their texts look like less obvious scams
Often scammers don’t want to make it less obvious. If it’s obvious and the mark falls for it, it’s a good indicator they’re on the hook and will fall for more. It’s to filter out the less gullible so the scammer doesn’t waste their time. Probably not the case with this situation specifically, but it holds true in general with scams.
Probably not the case with this situation specifically
Yeah :( High-value item already in hand, never a need to guide somebody which store to buy the giftcard at or what to say to the bank teller…
On a similar note, a reason why you shouldn’t respond to spam/scam texts because it basically verifies you as an active phone number. Why waste man/bot power texting numbers that may or may not exist when a majority of your texts will at least be seen by a human which will probably boost their chance
It’s why I tell my friends not to respond even tho some of their responses are really funny
Some smarter ones I see usually range between 2-7 lines of text usually written as a time sensitive question that will affect the totally real persons social or work like
One of my favorite ones was about 5 lines of text that was posed as a date
It was like “Hey Kayla it’s Mike, some short sob story about dating life, hope our first date goes well, then nonsense about dating with an address thrown in
However after the 5 lines it was in Arabic or some similar flowy characters and when I translated it continued “mikes” story about where he was from and how oh so sad his life was
Tldr totally fishing for a pity “sorry wrong number” to see if my phone number would be seen by human
the methods used by thiefs to try and get access to your phone data.
It is not about accessing the data but to disassociate the current user from the phone so that the thief can reset the phone or/and it’s components for new users.
Uhg! It’s outta control.
Does anybody have ideas for an anti-pick-pocketing solution they’d like to share? I might have to start a community for it. Or maybe you know some forums where designers who may be interested might be hanging out.
Requirements:
- retrofit almost any front pants/shorts pocket
- allow for near instant access (allowing for e.g. snapping a photo before the moment passes)
- one-handed access
- mechanical/passive: non-battery operated or fails in “unlocked” mode
- if not locked to owner’s hand (or say a finger-worn key), makes removal feel obvious
- automatically resets (resilient & inebriated person approved)
- ideally works with any phone case
- relatively inexpensive, and potentially even open source and/or 3D printable
Lately been imagining something like this, kinda… not really, and with only 2-3 fins:

so you gotta pull your phone out in a way that stretches the pocket to max width and one fin noticeably rubs against your leg.
Doesn’t meet all the requirements but also thought about a long and wide strip of cloth sewn at the bottom of a pocket that you could tuck into your waistband.
Edit: aware of one existing solution but not a huge fan

Mouse trap phone case. It fulfills almost none of the requirements, but it’ll be satisfying when a thief gets snapped.
Yeah it’s great the first time it works but then you have to spend 5 minutes looking for and assembling all the bits and pieces to set it up again.
Decoy phone that is actually a tazer, real phone in underwear.
Don’t get them mixed up…
Velcro sewn to just inside the top of your pocket, so sticking a hand in your pocket makes a loud noise and you can feel it, for any pickpocket to separate the velcro.
Oh my god, wallet chains are going to make a comeback, but for phones this time.
Next: pants sagging so much I can see 4" of crack
ahh the 00s
I use a fanny pack at large events.
Many have hidden zippers for wallet and phone, and its in front of you so its hard to steal from.
Thanks, phone theft is rampant in nightclubs as well and would be great to solve for the pocket problem.
Do like these guys (who I think spend a lot of money on marketing):

I got a cheap one from Amazon.
A key thing a look for are those little nylon pulls on the zipper handles. You can always add them to a zipper as well.
You can loop the pulls through each other to make it harder to open a zipper. I do this for backpacks since they’re behind me. This is more of a deterrent than a lock though.
I’ll send a pic after work to describe it. (Although there are actual products but I am cheap).
Also might wanna try to just bring a cheap phone you wouldn’t mind to lose just in case you do manage to lose it. Back up your data so if it does go missing you’ll have the memories.
That’s a great idea! Thank ve thought about carrying a decoy wallet before, but a decoy phone is also a great idea
Not a bad strategy at all.
Still, hate to negotiate with terrorists. And bring home potato photos. Instead of $developing-nation-per-capita-GDP phone quality photos.
Which of course means the thieves will still be tempted! If anti-pickpocketing strategy becomes too successful, they’ll move to violent means, then a cheap phone will be a must.
Well phones are generally pretty good for taking pictures and videos. A pixel 4 or something is a pretty decent phone for example.
Man, the last threat the author received was absolutely BEGGING for the navy seal copypasta lololol
But give them one of the more obscure versions so they don’t immediately realize what it is.
What’s this you’ve said to me, my good friend? Ill have you know I graduated top of my class in conflict resolution, and Ive been involved in numerous friendly discussions, and I have over 300 confirmed friends. I am trained in polite discussions and I’m the top mediator in the entire neighborhood. You are worth more to me than just another target. I hope we will come to have a friendship never before seen on this Earth. Don’t you think you might be hurting someone’s feelings saying that over the internet? Think about it, my friend. As we speak I am contacting my good friends across the USA and your P.O. box is being traced right now so you better prepare for the greeting cards, friend. The greeting cards that help you with your hate. You should look forward to it, friend. I can be anywhere, anytime for you, and I can calm you in over seven hundred ways, and that’s just with my chess set. Not only am I extensively trained in conflict resolution, but I have access to the entire group of my friends and I will use them to their full extent to start our new friendship. If only you could have known what kindness and love your little comment was about to bring you, maybe you would have reached out sooner. But you couldn’t, you didn’t, and now we get to start a new friendship, you unique person. I will give you gifts and you might have a hard time keeping up. You’re finally living, friend.
Hadn’t seen that one before. That’s a good one, lol
Why doesn’t anything this interesting happen to me!
As the author found out, these phones end up in Shenzhen. You can buy these burnt logic boards on the cheap and lots do just for testing. Check out Strange Parts on YT, he has soldered lots of boards and shows they sell them in bins. The grey market is the only place for them.
Also, for those that aren’t familiar with how Apple’s encryption works. The OS creates a key pair when you create your account, fully encrypting the contents. The contents become garbage if the key pair cannot be matched. This means even if you don’t remotely wipe the contents, the data they try to get from say recovery software or whatever, cannot be read. It’s of course good to wipe it remotely in case they guess your PIN, but if they can’t, then the data is gone forever. From a technical perspective, it’s actually pretty cool.
Android uses similar storage encryption (and you can activate encryption for an SD card if you have sensitive data on it), the encryption key is protected by a TPM or Secure Element chip or by ARM TrustZone or equivalent, it checks that the OS is unmodified before booting and the chip only gives the key to the CPU if the user enters the correct PIN
This made me realize, as an android user, I have no idea what I’m supposed to do if someone steals my phone.
Google has the same thing
Encrypt it with a strong password in the first place…
They have the same system. The phone is tied to your account and you can track, lock and erase it remotely with Google’s Find My Device.
Luckily I’ve only had to use “find my device” whenever my phone decides to catch-up with the TV remotes under the couch cushions
We have a black coffee table and sometimes it’s just on the coffee table and I’m like “Jesus fucking Christ what is wrong with you.”. In fairness to me, it’s summer, I keep the shades drawn, keeps the temps down.
Luckily google keeps track of your every movement by default 🙂
Yeah and apple doesn’t…
?
I also fucking hate Apple, with the same seething rage that redhats hate Windows, and I too must admit this is shockingly effective security.
Someone’s going to sell your phone on the black market
is my favorite
Oh no! Then I won’t have my phone anymore!
Wait just a second…
deleted by creator
“I’m too smart and superior for smartphones. I know that noone asked, but I think it’s important to share that information. I also can’t be bothered to read any part of the article I’m commenting on, considering it doesn’t apply to me (being so smart and superior by not having a smart phone). Can someone answer my question that I wouldn’t have needed to ask if I read 5 sentences?”
deleted by creator
You sound fun at (key signing) parties
deleted by creator
Dude why even comment?
deleted by creator